Create a GPG key on macOS and Linux
Context
GPG stands for GNU Privacy Guard, which implements the OpenPGP’s specification (RFC 4880) and is a free software implementation of Symantec’s PGP cryptographic software suite.
What’s used for?
We use it to encrypt and sign data to attest its authenticity. For example, we
use it to sign our commits while using a VCS like git, or sign e-mails. So we’re making
it clear that we, in fact, did write the said commit, or the e-mail.
How’s it possible? Because not only we’re assigning an identifier to our messages, but
we can include things like email address and our real name, also anything that we want
to include to make sure of our identity may be included in the comment section of the key.
So let’s create our own GPG key using either macOS or Linux environment.
Creating
You must use a specific software to generate the GPG key. I use gnupg, which can be used in both Linux
and MacOS environments, but you can use anything that’s OpenGPG compliant. You must also install a GPG agent,
but it will depend on your OS.
In a terminal, issue the following command, and follow the prompts:
gpg --full-gen-key
I prefer the following configuration:
- 1 (RSA and RSA)
- 4096 bits
- 6m (6 months)
And there are some prompts for identification:
- Real name
- Email address
- Comment
Also, it’s going to ask for setting up a password. It’s optional, but I highly recommend using one. Then, you’re set!
Listing
To list your GPG keys:
gpg --list-secret-keys --keyid-format SHORT
[keyboxd]
---------
sec ed25519/KEY_ID (SHORT) (CREATED_AT_DATE) [SC]
KEY ID (LONG)
uid [ultimate] REAL_NAME (COMMENTS) EMAIL_ADDRESS
ssb cv25519/REDACTED (CREATED_AT_DATE) [E]
It’ll list all your keys stored in your keychain.
Exporting and importing
If you need to export the public key to a service that may interact with your GPG key, issue the following command:
gpg --armor --export SHORT_KEY_ID
-----BEGIN PGP PUBLIC KEY BLOCK-----
THIS IS REDACTED
-----END PGP PUBLIC KEY BLOCK-----
To export your GPG key to another environment (it’ll ask you to enter your key’s password if set):
gpg --export-secret-keys 67F2F4737DF32288 > pkey.asc
ls -lha ./pkey.asc
-rw-r--r-- 1 carlosdmz root 693B Mar 23 13:57 pkey.asc
To import:
gpg --import pkey.asc
Signing commits in git
To do this, you need to edit a file called .gitconfig, which is usually under your
$HOME directory. So it should be something very similar to this:
[user]
name = <YOUR_NAME>
email = <YOUR_EMAIL>
You’re going to add one config row under the [user] and, optionally, add a [commit] section and
add another config row, which is pretty much in a toml format. The [commit] change is optional,
but highly recommended if you want to sign your commits by default:
- Under
[user]section, you need to add thesigningkeyand pass your key ID, which you can check by listing your GPG keys; - Under
[commit]section, add thegpgsignand set it totrue. With that,gitwill automagically sign your commits using the GPG key you referred in thesigningkeyconfig previously.
[user]
name = YOUR_NAME
email = YOUR_EMAIL
+ signingkey = KEY_ID
+ [commit]
+ gpgsign = true
And now, every commit that you do, it’ll sign your commits right at the end.
If you’ve set the gpgsign to true, it’ll do that by default. If you don’t,
you need to use a flag in the git commit command to tell that you want
to sign the commit with the key you’ve set under [user], which is the -S.
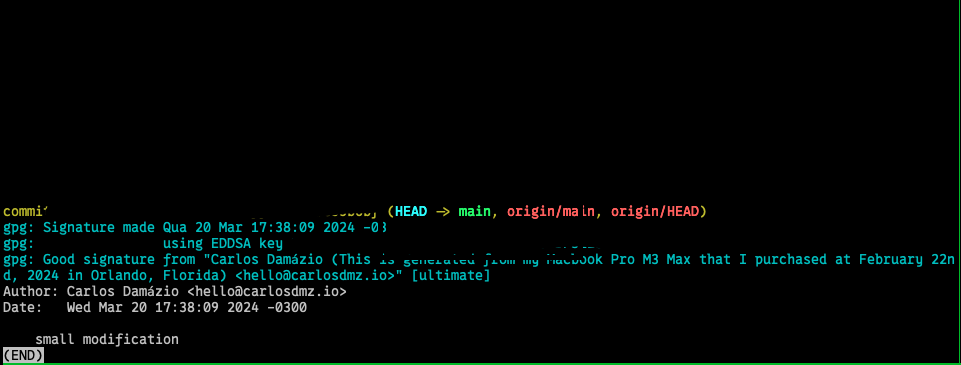
If you check the log history using git log --show-signature -1, you may check
if the commit has a good signature: